Why Netrix
See how our people, processes, and technology set us apart.

Solution Areas
We partner with you to build business-critical solutions across six key areas.

Learning Center
Explore resources like best practices, user training, trends, news, and more.

ABOUT NETRIX GLOBAL
Holistic Approach to Cybersecurity & IT Challenges
Netrix Global is an award-winning MSSP and MSP that designs, delivers, and supports business-critical solutions for our clients across the full spectrum of their complex, risky, and ever-changing IT infrastructures. While other providers deliver commoditized projects that only address point-in-time challenges, we are unique in how we partner with our clients to achieve real business outcomes that create lasting value. By continuously evaluating clients’ evolving needs, we ensure that their solutions are always on, always secure, and fully modernized.

WHAT MAKES US DIFFERENT
Achieving Real
Business Outcomes
What makes us different is our relentless pursuit of our clients’ best interests. We are very selective in our hiring practices, so our clients work with only the most accomplished engineers, solution architects, and service professionals. You will never get our “B team” because we don’t have one. We provide the highest standards of service, which includes rapid response times to client outreach, fast resolution to issues, and ongoing monitoring of your environment.
POWERING BUSINESS FORWARD
Keeping Our Clients
Ahead of Market Disruptions
We’ve all heard the words of caution shared by leading business strategists, investors, and technology leaders, “Adopt AI, or you’ll be out of business.” AI will soon become a fundamental part of our business infrastructures, changing the way we work, learn, travel, and communicate with each other. So how do you intelligently invest in AI quickly, since the manual on adopting this maturing technology continues to be written? Finding practical uses that drive real business outcomes takes a strong understanding of AI capabilities but an even stronger understanding of the root business challenges. Our methodology backed by our teams of data, AI, and ML experts, will keep your investments in AI strategic and your goals attainable.

Aligned Solutions
We will only recommend services and approaches that serve your greatest needs and that lie within your budget.
Smart Investments
We will never encourage you to invest in technologies unless they achieve lasting, measurable results against your defined objectives.
True Partnership
No one knows your business the way you do, that's why we've honed a focused approach to listening at the forefront of every engagement.
Cybersecurity First
Cybersecurity is at the forefront of everything we do. This is one reason Microsoft chose us as one of its first Managed XDR validated partners in 2022.
Results-Driven
It's all about the results. We help clients achieve measurable impacts across an ever-growing list of challenges.
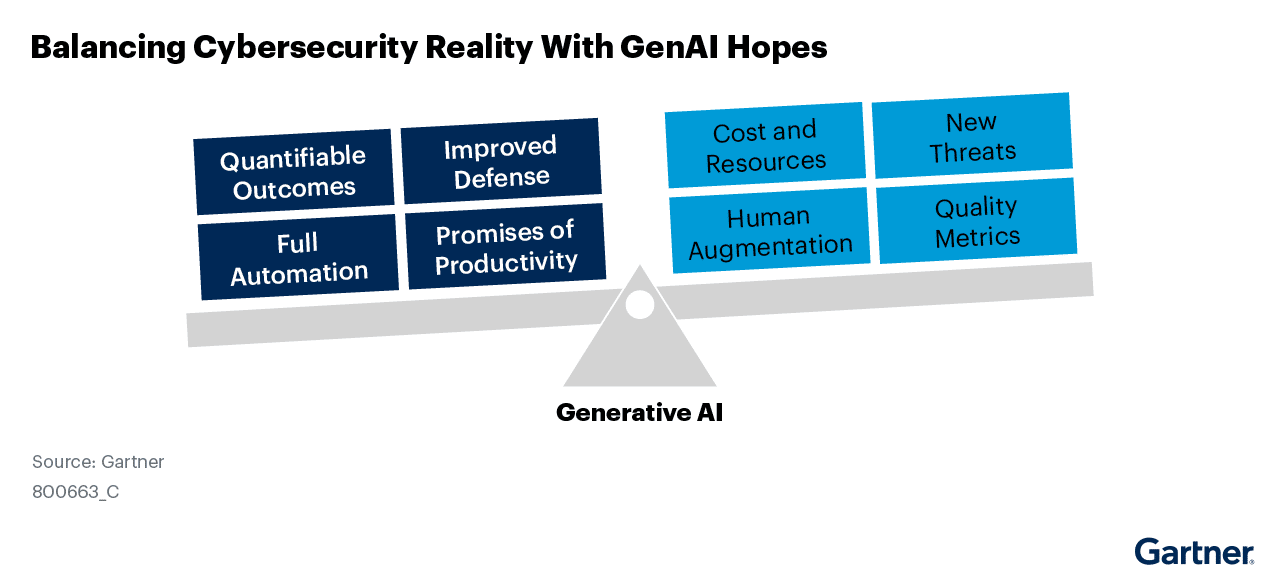
2024 SECURITY TRENDS
Predicts 2024: AI & Cybersecurity - Turning Disruption Into an Opportunity
Delivering The Highest Standards of Service
Turning Your Obstacles Into Opportunities

Keeping Your Business Secure >
Actively defend against cyber threats 24x7 and keep your business protected from loss and downtime suffered when an attack inevitably occurs.

Staying Competitive in Today's Markets >
Digitally transform your business through modern tools and applications to stay competitive in changing landscapes and venture into new markets.

Finding Cost Efficiencies >
Decrease your infrastructure TCO and uncover cost efficiencies while you change your IT department from a cost center to an agile innovation hub.
Filling Gaps in Your Skills & Schedules >
Get your IT teams the support they need for administrative tasks and refocus your internal resources on driving your business forward.
Jump into Action When Ransomware Strikes
When ransomware took down this national food manufacturer’s systems during an off-hours event, they needed a partner that could spring into action quickly and keep their business from further loss.
Building Solutions
Across Six Key Focus Areas
At Netrix Global, we continually work to provide the tools and technology that companies need in the ever-evolving digital landscape.

Cybersecurity
Cybersecurity

Outsourced IT
Outsourced IT

Cloud Infrastructure
Cloud Infrastructure

Application Innovation
Application Innovation

Modern Work
Modern Work

Data Intelligence
Data Intelligence
Take a Look at Our Robust Portfolio of
Integrated Services
Our solution areas are backed by a portfolio of services and capabilities that help us develop an IT vision designed specifically to meet your business objectives.
What's New
with Netrix Global
Check out our recent announcements and press coverage.
Get Started Towards a More Profitable Business
No matter what challenge you’re facing today, our team of technical experts can get you started on a path towards a winning, more profitable business that is always secure.